Defect Resolution in software testing is a step by step process of fixing the defects. A Defect in Software Testing is a variation or deviation of the software application from end user’s requirements or original business requirements. A software defect is an error in coding which causes incorrect or unexpected results from a software program which does not meet actual requirements.
- The defect density is the ratio of the number of bugs found in software over a certain period to the size of the program or its individual part.
- Preventative tests are designed early; reactive tests are designed after the software has been produced.
- JIRA includes features that allow teams to send email alerts, share screenshots or videos of the defect, and offers roadmaps, reports, and insights over the course of the project.
- Risk-based Testing is the term used for an approach to creating a Test Strategy that is based on prioritizing tests by risk.
- The case where one software bug prevents the finding of another.
- It also tries to look for the Dot Matrix Printer , when the app cannot locate the laser printer.
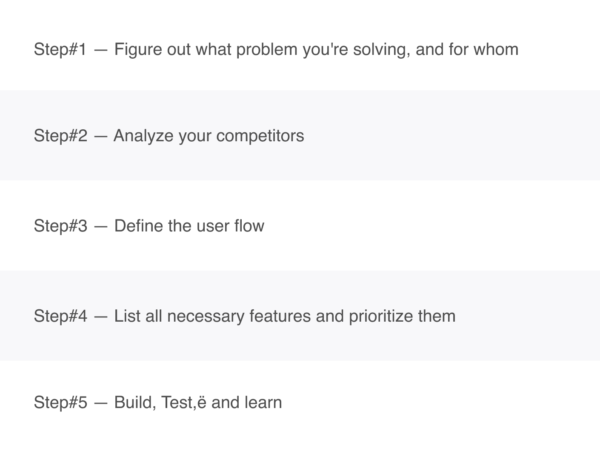
- This process can be easier and more convenient with the proper plan and resources.
It offers teams the ability to securely manage software development projects, share files, manage calendars, and track project milestones. SmartSheet offers a range of customizable templates for defect tracking to build a workflow that can be molded to fit any team’s needs. Since the latent defect in the app was not tested for DMP and this sort of condition was not experienced while utilizing the laser printer, this flaw was never identified. This means while the testing, above-mentioned situation was not experienced. Exploratory testing is a hands-on approach in which testers are involved in minimum planning and maximum test execution. The planning involves the creation of a test charter, a short declaration of the scope of a short time-boxed test effort, the objectives and possible approaches to be used.
Data Visualization for Better Debugging in Test Automation
For example, in the above scenario, when the development team reported that they already fixed 61 defects, your team would test again to verify these defects were actually fixed or not. If the defect is successfully fixed, the testers mark it as closed. If not, then this part of the program is sent for revision so that the developer can eventually get rid of the problem. After working on bugs, you need to check if everything is working correctly. At this stage, testers join the work again to track unresolved and new defects.
There are high, medium, and low likelihood defects based on this criterion. When risk assessments are made for planning tests, the test designers frequently use this information to concentrate on these areas, sometimes referred to as hotspots. The term “defect clustering” refers to the situation https://www.globalcloudteam.com/glossary/defect-masking/ in which a small number of modules include most of the reported flaws and operational failures. Defect categorization help the software developers to prioritize their tasks. That means that this kind of priority helps the developers in fixing those defects first that are highly crucial.
Defect causes
The app, however, by default always chooses laser printer options. As consequence, when the print command is introduced, printouts come out of the laser printer. It also tries to look for the Dot Matrix Printer , when the app cannot https://www.globalcloudteam.com/ locate the laser printer. The app tries to print using DMP but generates an error message again and again. An app to print employee salary slips provides two different printer options i.e. laser printer, and dot matrix printer.
The tracker can also be used to log any updates or changes made to address the defect. This allows testers to keep track of corrections and retest to check whether the defect was fixed or update any additional defects found. A defect tracker can be helpful in identifying the cause behind defects as well since log files and reports or descriptions are generally included to elaborate on the defect. Continuing the first example, where an app cannot be tested for DMP, two additional issues are masked i.e. RavinderDotMartix printer is never searched if a Laser printer is found.
How to Reduce Costs & Optimize Testing Process of Salesforce Apps
By adopting a comprehensive testing approach, development teams can increase the likelihood of unmasking hidden defects and ensuring the overall quality of the software. Automation plays a crucial role in identifying and preventing masked defects. Organizations can achieve comprehensive test coverage and effectively address hidden flaws by leveraging automation tools.
Automation enables the execution of a wide range of test scenarios, including regression and exploratory testing, which may be challenging to cover manually. Automation tools can handle repetitive tasks, execute tests precisely, and detect unexpected behaviors or hidden defects that may arise under specific conditions or inputs. This helps to unmask defects that may have been missed during manual testing, ensuring higher software quality and reducing the chances of masked defects going undetected. Regular code reviews and robust quality assurance practices mitigate the risk of masked defects. Developers identify issues and areas for improvement through code reviews, while static code analysis tools detect coding errors and enforce best practices. Maintaining high code quality minimizes the likelihood of hidden flaws remaining undetected.
Top 10 Automated Software Testing Tools
The code coverage testing tool runs parallel while performing testing on the actual product. The code coverage tool monitors the executed statements of the source code. When the final testing is done, we get a complete report of the pending statements and also get the coverage percentage.

Masked Defect is a type of defect that is hidden in the software and hasn’t caused a failure, because another defect has prevented that part of the code from being executed. It is only uncovered when the defect hiding it is uncovered by the user, by performing a specific operation. Defect analysis considers information on particular defects, defect priorities, product problems, history of defect resolution, developers involved, and other factors.
Q. 32: While monitoring your project what all things you have to consider?
Both self and peer reviews are powerful tools for learning and motivation. After the software has changed or when the environment has changed Regression testing should be performed. Provide developers and other parties with feedback about the problem to enable identification, isolation, and correction as necessary. When a “flow of data” through an information system is graphically represented, then it is known as Data Flow Diagram.

The module required for calculating salaries has an unidentified defect. This prompts the database to convey wrong salary numbers which are further reflected in the annual salary calculations, tax calculations, and balance sheet. The cause of such error is that ignoring other printers if an earlier searches return a found response. Instead if printers are found from a pool of printers, then such masked error will not arise. Understand why fault Injection is a complementary technique in software testing for improving softwa… Why understanding Regression Defects benefits your Release Cycle Understand key practices that can be deployed to prevent regression defects and benefit your release…
The Ultimate Testing Terms Glossary: A Reference for Testing Professionals
This, in turn, helps determine the nature and quality of the defect management process in software testing. Integration testing is a level of software testing process, where individual units of an application are combined and tested. Defects can be classified into different types based on various criteria, such as severity, priority, frequency, origin, or impact. For example, a defect can be categorized as critical, high, medium, or low severity depending on how much it affects the functionality, reliability, or safety of the software. Similarly, a defect can be assigned a high, medium, or low priority based on how urgently it needs to be fixed. Other common defect types are functional, non-functional, cosmetic, performance, security, compatibility, or usability defects.


